SECURITY
EVALUATION
A thorough security analysis of your application or architecture ensures that all security enhancements in your product design process are applied in the most effective and efficient way.
WE HELP
COMPANIES DEVELOP
SECURE PRODUCTS
CYBERCRYPT's decades of experience in cryptography, security architecture, and security analysis keep your products protected.


“We at BEUMER Group have used CYBERCRYPT to help assess the security in a selected SCADA web application both on the server and client sides. CYBERCRYPT has demonstrated its high expertise in security analysis and cryptography by quickly identifying areas where the security might be further improved. There has been a professional and pleasant dialogue regarding different evaluations of risks and possible changes to concrete implementations and strategic decisions. The engagement with CYBERCRYPT has helped us to raise the security awareness within our product development department. All in all, our impression of CYBERCRYPT’s work is highly positive.”




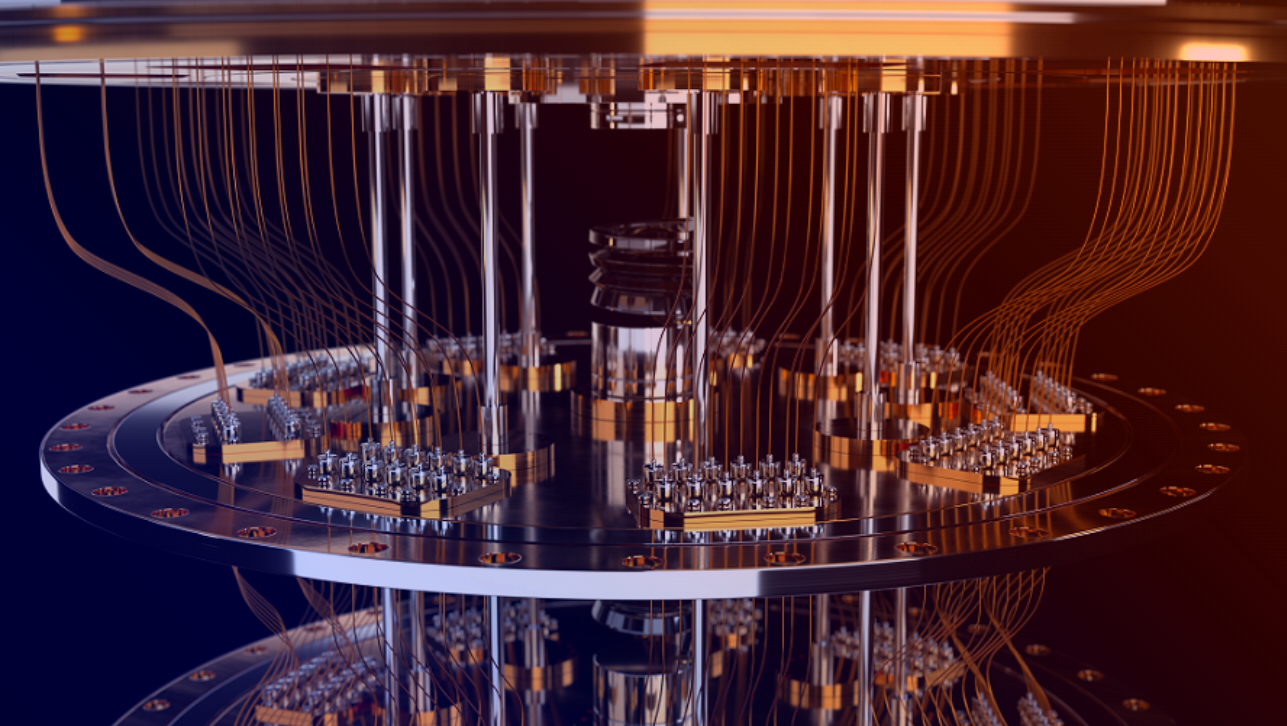

CYBERCRYPT D1
WE PROTECT YOUR
DATA HOLISTICALLY
Protection of data in applications is a necessary layer of defense against today’s attackers. We protect your databases, messages, object stores, and more across data centers, cloud environments, devices, and apps.
PROTECT YOUR
ASSETS - SECURE
YOUR PRODUCTS
Security is our heart. We provide expert services and solutions, so that you can deliver your products to market. All the while, we safeguard not only your critical data, but also that of your customers.
WE PLAN FOR YOUR
LONG-TERM SUCCESS
By implementing the proper cryptography and cyber resilience paradigm, we ensure that your products achieve the highest protection standards throughout their lifecycle.

A thorough security analysis of your application or architecture ensures that all security enhancements in your product design process are applied in the most effective and efficient way.

With your specific needs in mind, we create the most effective security architecture for your product, elevating it to the next security level.

We implement your product's new security architecture. Via a detailed project plan, we support your responsible teams, throughout the process, in their production environment.

Your product should meet its security goals throughout its lifecycle. By training your key personnel, we help you to remain at the forefront of security technology.
About us
EXPERTS IN CRYPTOGRAPHY AND SECURE PRODUCT DESIGN
We constantly strive to leverage our combined knowledge and expertise in order to ensure maximal protection for your products.
At CYBERCRYPT, we establish the foundations of product security using innovative, advanced cryptographic solutions.
SECURE PRODUCT DESIGN FOR EVERY INDUSTRY

Our Vision
STRONG PROTECTION FOR EVERY PRODUCT, ROBUST CRYPTOGRAPHY IN EVERY DEVICE
Your assets, along with those of your customers, may be endangered by attacks that exploit vulnerabilities in your product's architecture, cryptography, and implementation. These new digital challenges demand designer security implemented using state-of-the-art security technologies and cryptographic primitives.




Sankt Annæ Plads 13
1250 Copenhagen
Denmark


Maximiliansplatz 22
80333 Munich
Germany


Hegibachstrasse 47
8030 Zurich
Switzerland


228 Park Ave S # 300
New York, NY 10003
USA
We are
the cryptography
and security experts
At CYBERCRYPT, we combine decades of experience in cryptography, secure architecture, and security analysis to keep your product protected.